Recently, a fake game called StarsVaders started circulating on Discord. Similar to other malware on that platform, it aims to trick users into downloading malware instead of an actual game. This malware’s real goal is to steal information like browser history, tokens, and other personal data.
In this article, we’ll break down how StarsVaders works, including:
-
Static Analysis: Looking at the file properties and hidden details that reveal it’s not a real game.
-
Dynamic Analysis: Running StarsVaders in a test environment to see what it tries to do on the system.
Along the way, we’ll use tools like FlareVM, VirusTotal, and Hybrid Analysis to help us uncover the true nature of this fake game.
By the end, you’ll see how attackers hide malware in plain sight—and how to spot it.
Discovery #
The phishing link was obtained through a friend, who mentioned the scam in a mutual Discord server. The messages were sent by a friend of theirs but they seemed suspicious. I asked them for the link and started with the analysis.
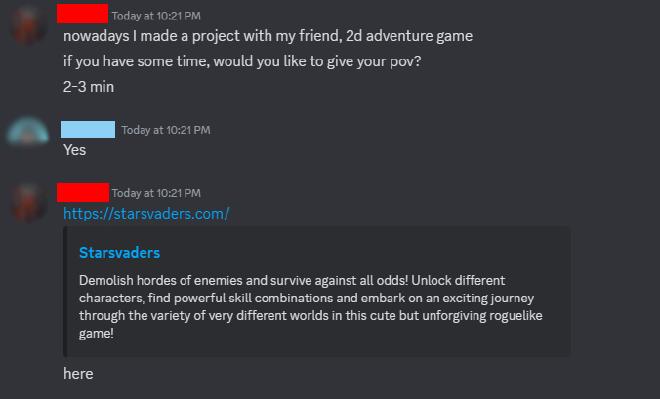
I first checked the website in VirusTotal, who.is, and URLScan and saw that the it was marked as malicious by a few vendors. The domain was created in September 2024, which indicated potential suspicious activity.
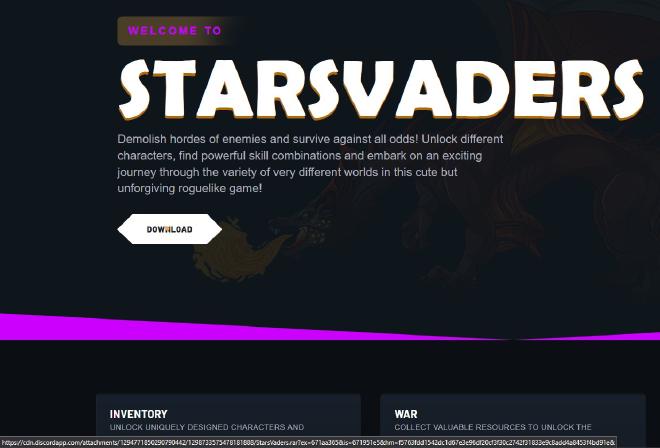
When I opened the website on my VM, I noticed a large “Download” button on top of the page. It also had various screenshots of the alleged game. I looked into this and identified that they used images from a game called The Braves while the malware was attempting to impersonate an upcoming game called StarVaders.
The previously mentioned “Download” button utilised Discord’s CDN to host and spread the malicious file. The attackers used this as it looks benign due to gamers being very familiar with Discord. This also makes it easier for the adversary as they do not need to spin up any extra infrastructure to spread the files.
Analysis #
Static Analysis #
After downloading the archive, I opened it and found an executable within it. I attempted to extract it, but the archive required a password to complete the extraction. I would assume the attackers provided the password to the victims. I had no such luck as my friend did not fall for the phishing attempt.
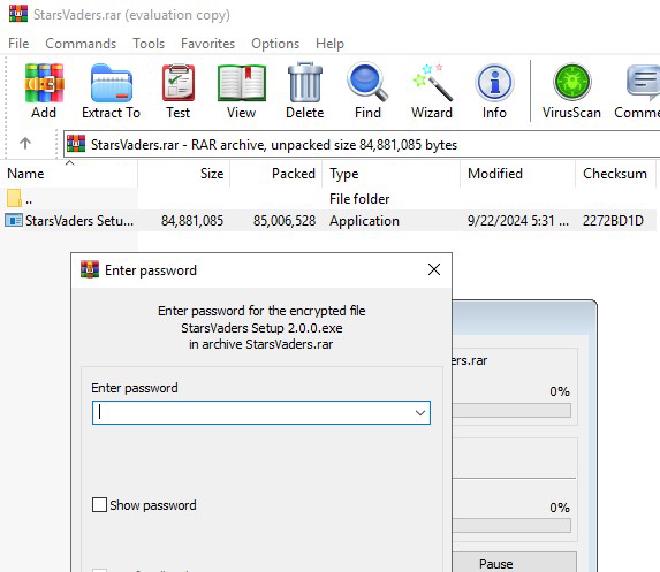
I decided to use John The Ripper’s module called zip2john which is used for password protected zip files. Thankfully, the password was within the rockyou.txt password dictionary file. The password was revealed to be beta.
I used FLOSS to extract strings from the file in order to obtain an initial understanding of its capabilities. FLOSS is a great too for such tasks as it can identify obfuscation and attempt to make it human-readable. In this case, since the file was too big, FLOSS essentially worked as the Linux binary strings. Observing the output indicated that the file is capable of manipulating the user’s clipboard and registries.
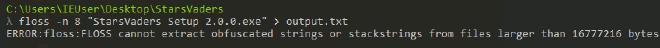
Running the installer dropped multiple other binaries. FLOSS showed similar results on the other files.
Dynamic Analysis #
As mentioned, the installer dropped more binaries. The files were located in the following directories:
AppData\Local\starsvaders-updaterAppData\Local\Programs\StarsVaders
The former directory contained one file named installer.exe. The file was identical to the initial installer StarsVaders Setup 2.0.0.exe which would indicate attempts at persistence. I, however, could not identify any indicators of persistence within the registries and/or scheduled tasks.
The other location featured more files:
StarsVaders.exe- main executable.Uninstall StarsVaders.exe- alleged uninstaller.- Chrome/Chromium-related files.
- Electron-related files.
elevate.exe- within theresourcesdirectory.
The main executable, StarsVaders.exe, contained the main functionality of the malware. It attempted to steal data from the user’s browser (cookies, history, etc.).
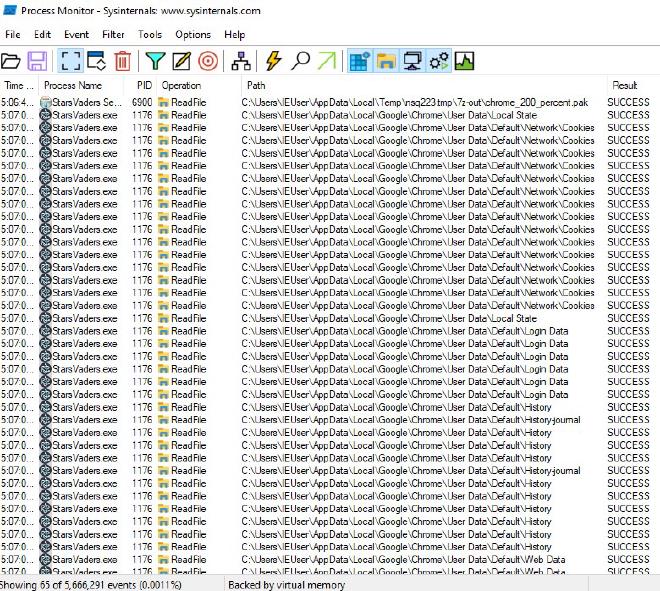
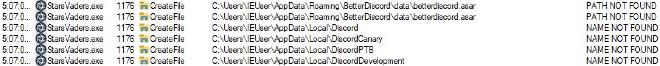
It also attempted to access files within the Discord directories within AppData. The files covered all versions of Discord (Discord, Canary, PTB, Development) and even the custom version of the application called BetterDiscord.
Examining the process tree showed that StarsVaders.exe ran two commands multiple times:
powershell.exe /c "Get-CimInstance -className win32_process | select Name,ProcessId,ParentProcessId,CommandLine,ExecutablePath"
C:\Windows\system32\cmd.exe /d /s /c "powershell -Command "& {Add-Type -AssemblyName System.Windows.Forms; [System.Windows.Forms.MessageBox]::Show('The application was unable to start correctly (0xc000007b). Click OK to close the application.', 'Application Error', [System.Windows.Forms.MessageBoxButtons]::OK, [System.Windows.Forms.MessageBoxIcon]::Error)}""
The former command functions similarly to pstree, while the latter shows a fake error message to trick the victim.
The uninstaller removed the files from the main directory but the installer within AppData\Local\starsvaders-updater remained.
The final file of interest, elevate.exe, is a file used by Electron applications. It does what the name suggests - it elevates the application’s privileges, providing it with higher access to the OS.
Finally, I decided to test how the application exfiltrates the obtained data. I did this by running inetsim and wireshark on a Linux VM and placing both VMs on the same Host-Only network adapter. The malware did not appear to download any additional payloads but it made a connection to a URL called unity-api[.]net. I could not directly access the domain due to CloudFlare blocking my attempts. This prevents me from further researching the malware’s capabilities.
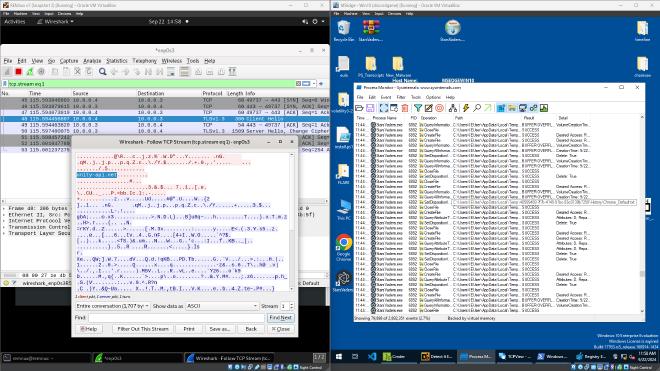
While this URL might look benign, VirusTotal and who.is indicated that it was created on the 31st of August. It would highly unlikely that Unity are hosting their API on a nearly brand-new domain.
Conclusion #
After the analysis, I gathered all of the evidence and reported the URLs to the providers which were used to host the websites/servers.
As of today, the archive file from the Discord CDN is unavailable.
IoCs #
Links #
www.starsvaders[.]com - VirusTotal
unity-api[.]net - VirusTotal
Hashes #
StarsVaders Setup 2.0.0.exe
ea2b7e73659c251243f33999c5b0e12bf6c180f44ff545a02acb7164eda8cd83
StarsVaders.exe
4d05d719f2af8bcb4e706d7b01ed54739fc63dd20579b17ef34c78e9a2e57a6e
StarsVaders.rar
9532a0f831316fd17b4089afc87950c472ab8ed5b58e0b2765d1d4fe8557557e
Uninstall StarsVaders.exe
47b6d08004a15d0bc8ac07f1a03d487cf287203e71024d438b2f503017ef8e6a
elevate.exe
9b1fbf0c11c520ae714af8aa9af12cfd48503eedecd7398d8992ee94d1b4dc37
installer.exe
ea2b7e73659c251243f33999c5b0e12bf6c180f44ff545a02acb7164eda8cd83
